
The right to access is a fundamental right contained within many data protection regulations globally. In particular the EU and UK General Data Protection Regulations. The right to access can often cause headaches for business. Tens of thousands of Data Subject Access Requests are made every month and sadly, many are not fulfilled properly. Many poorly fulfilled DSARs then result in complaints to a Data Protection Regulator.
To put this in perspective, in the financial year 2021/22, the UK Information Commissioner’s Office (ICO) received 36,343 complaints*. Of that number, a whopping 37%, well over a third, related to the right to access. What these complaints (both merited and unmerited) show, is there is significant room for improvement in the way DSARs are handled.
What is surprising, given the ICO complaints statistics, is that very little work has gone into developing a model that supports the fulfilment of Data Subject Access Requests specifically. Such a model would be extremely helpful in ensuring DSARs were managed in a manner that provides the data subject with the information they need in an efficient manner. Such a model could materially reduce the burden on controllers and thus reduce the likelihood of a data subject making a complaint to the ICO. Well, we looked around and couldn’t find anything so, rather than lament the lack of such a model, we created one. We are very proud to present to you, the reader, the Right to Access Fulfilment Model (RAFM).
The Right to Access Fulfilment Model (RAFM) was inspired by the efficacy and simplicity of the Electronic Discovery Model (EDRM). The RAFM does to the right to access what the EDRM does to e-Discovery. It aims to help anyone – not just DPOs or Privacy Professionals – work through a Data Subject Access Request in a logical, consistent, and repeatable manner.
In a similar way to the EDRM, the RAFM represents a conceptual view of the end-to-end process. The RAFM is a universal model that can be applied to support the right to access in any number of jurisdictions. Whether you’re operating under GDPR in the EU or UK, POPIA in South Africa, CCPA in California, or, LGPD in Brasil, the RAFM is a model that, if applied correctly, will allow your organisation to demonstrate accountability in relation to upholding a data subject’s right to access. The RAFM is a universal model. This means an organisation operating in more than one legal jurisdiction, with some local tweaking here and there, can operate a single set of core processes to deal with the right to access. Equally so, a processor operating anywhere in the world could develop processes to support this model and thus serve controllers in whichever data protection jurisdiction they operate.
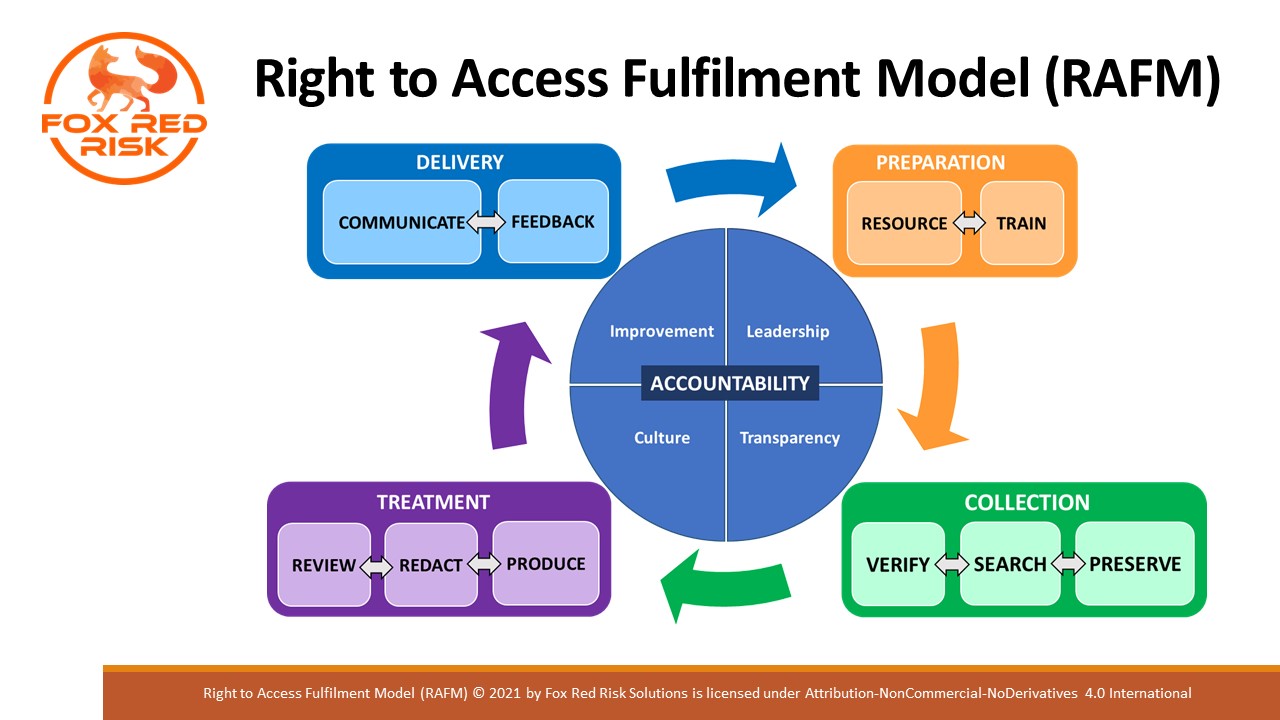
As is depicted in the image above, the RAFM is broken down into four distinct phased components of Preparation, Collection, Treatment and Delivery, with a hub component of Accountability. Each phase follows on from the previous in chronological order. Each phase, however, contains iterative sub-processes. The sub-processes are iterative in nature because an output created in one sub-process may require further work in a separate sub-process before moving to the next phase.
For example, material submitted for review in the treatment phase may not have been redacted correctly and the material may require more, or less, redacting before it is resubmitted for review. Searches performed at the collection phase may identify a significant amount of personal data and may warrant a controller asking a data subject if they would be willing to be more specific with their request.
The four-phased components of the RAFM are bound to an overarching Accountability “Hub”. Accountability is a fundamental principle of good data protection governance. It is only logical, therefore, that accountability encapsulates the RAFM. Accountability manifests itself within the model in four ways – leadership, transparency, culture, and improvement.
Preparation: The preparation phase has two iterative sub-processes and aims to ensure an organisation has effective resources to fulfil DSARs and, in addition, that those resources are effectively trained. The resource and train sub-processes are iterative because as employees rotate in they will require training, and as processes change and develop training will need to be updated with employees then being trained in the new material. For example, if a new case management tool were to be deployed those operating that tool would need to be trained in its use.
Collection: The collection phase has three iterative sub-processes – verify, search, and preserve. The collection phase aims to collect the material requested of a data subject in the most efficient manner possible. The first sub process, verify, seeks to ensure the request has been validated in terms of content, scope, and the identity of the data subject. The second sub-process, search, seeks to ensure the requested material is found, potentially across many systems, and is complete. The third sub-process, preserve, seeks to ensure that any material identified in the search is protected from deliberate or accidental destruction or alteration. The latter part is particularly important should a data subject make a complaint to a regulator as a controller would then be required to defend their processes. Once completed the material is then moved into the treatment phase.
Treatment: The treatment phase has three iterative sub-processes – review, redact and produce. The treatment phase aims to take the data collected in the collection phase and reduce this down to a final subset of material. The final subset of material is achieved by conducting a review to identify duplication, third party content and exempted material. The reviewed material then enters a redaction phase where exempt material is removed. Redacted material is reviewed again before a final redacted subset is approved for production. The production sub-process then takes that final set of material and packages it up with any relevant supporting information ready for delivery to the data subject.
Delivery: The delivery phase has two iterative sub-processes – communicate and feedback. The delivery phase aims to take the production ready subject access ‘pack’ and deliver it securely to the data subject in a manner that allows the data subject to easily access the material. The delivery phase also aims to make the provision of feedback to the data subject, and other relevant stakeholders, as efficient as possible. Furthermore, feedback could include applying other data subject rights arising from the DSAR, such as a rectification request or a request to restrict processing, and finally, communication may include communicating with the Data Protection Authority in the event of a complaint…but hopefully not!
So that’s the RAFM in a nutshell. A simple model that will help you visualise the various processes that go into fulfilling a Data Subject Access Request. Four phases with iterative sub-processes that, if implemented effectively should make dealing with even the most complex DSAR a doddle. Well, maybe not a doddle but definitely easier than it may have been!
Want to learn more?
For a deeper dive into each aspect of the RAFM and to learn how to implement the RAFM in your organisation, read our book “Managing Subject Access Requests: A Practical Guide for EVERY BUSINESS“. Now available in all good books stores.
- Current stats are available here: https://ico.org.uk/about-the-ico/our-information/complaints-and-concerns-data-sets/data-protection-complaints/


