

Is your supply chain resilience programme reminiscent of the article image? Aged, poorly maintained, complex, hard-to-untangle. Do you carry out due diligence at the beginning of your engagements? More importantly, do you carry out ongoing governance and oversight? Even more importantly, does supply chain resilience form part of your wider operational resilience strategy or business continuity management system (BCMS)? Whilst many may be breathing a sigh of relief that the incident at Travelex didn’t happen at their organisation, it is clear the ransomware incident is still having a wider impact. In a world where companies outsource so much of their internal operations to third parties, it is even more critical than ever that supply chain resilience is given top billing.
What happened at Travelex?
Travelex was infected over the 2019/2020 Christmas and New Year period with ransomware. The particular ransomware is believed to be Sodinokibi which has been known about since at least April 2018. The infection is believed to have exploited unpatched vulnerabilities on the organisations VPN software. Patches have been available for this software since at least May 2018.
Once Travelex was infected they have been frantically dealing with the resulting impacts of the attack. Recovery efforts at the time of writing are up to 13 days with only a glimmer of hope that things will soon get back to normal. The UK site is still showing the following:
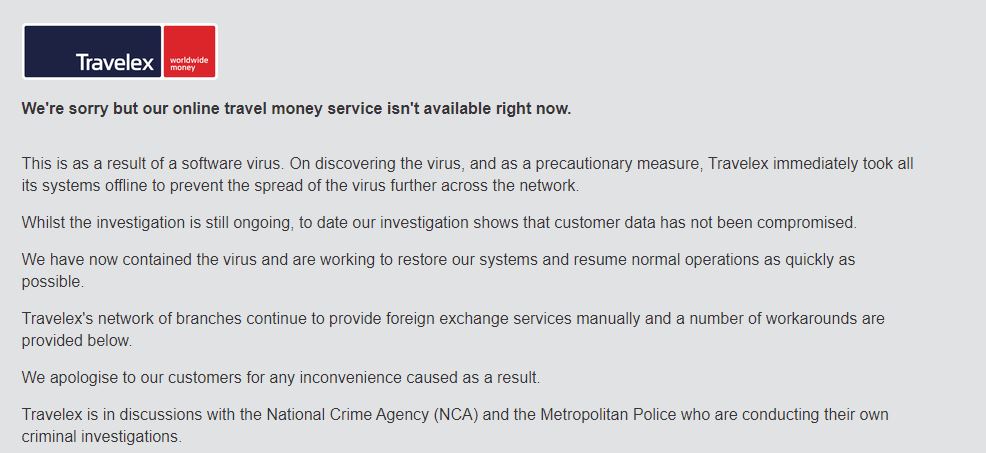

Wait a minute!! If Sodinokibi was a known threat why didn’t it get picked up by their Anti-Virus?
Bypassing AV can be done if you have some rudimentary knowhow. There are video tutorials on YouTube such as this “Bypassing AV with Metasploit” that have been around since 2008. Even with the advent of sandboxing, reputational scoring and heuristics, AV can still be circumvented. Whilst some malware organisations are marketing Artificial Intelligence (AI) in their products, what is actually being done is Machine Learning (ML) and that means the system pretty much is restricted to inferring from what it has learned within a training set of data. Such ML products can also be circumvented where the malware is operating outside of what the ML engine has “learned“.
That said, just because AV can be circumvented, it would be insane to throw out your AV tools. Doing so would just mean you would be flooded with all the malware that can currently be detected – such a policy would cripple your organisation in no time at all! A good practice is to use two separate AV products. One at the desktop level (such as Windows Defender Antivirus) and a different AV product on your server infrastructure. That way you benefit from two different signature databases. Remember, from a supply chain resilience perspective, it’s important you don’t infect your supply chain just as much as they don’t infect you!
In terms of protecting your organisation from ransomware, I cannot stress enough how important patching and vulnerability management should be in your information security strategy. I know that patching has it challenges but there is a pretty common-sense truth that:
“Hackers can’t exploit a vulnerability that no longer exists!”
Make sure you patch more than just the Microsoft security patches because limiting your programme to just MS OS patching (and patting yourself on the back for meeting your 14 days patching SLA) is going to give yourself a massive fall sense of security.
Another good practice is to install appropriate DNS-based web-filtering and ensure the tool is configured properly. Ensure new domains and uncategorised domains are blocked by default. That way any beaconing activity can be swiftly contained. Apply blacklisting rules on your firewalls for known bad IPs. There are multiple open-source threat intelligence sources available so this can be done pretty cheaply if you have the knowhow – or you can ask us at Fox Red Risk!
The other very good practice is to reduce access. Simply applying the age-old techniques of segregation of duties and least privilege will do wonders to stop the spread of a ransomware outbreak. Admins, Local Admins and Domain Admins should have separate escalated privileges accounts. These accounts should have no email accounts and no access to the Internet. All their activity must be logged and monitored daily.
Finally, you need to be logging and ideally, you need a SIEM tool. Get a SIEM managed service if you don’t have the capability in-house, again we can help with getting you setup with a solution. At the very least ensure you have central-logging enabled and monitored. If you are compromised then at least you can work out how it happened.
Why is it a Supply Chain Resilience issue?
Have a look at the following quote from Reuters. They reported that Travelex is:
“…are now at the point where [they] are able to start restoring functionality in [their] partner and customer service.”
As you can read from the quote they are prioritising their partner functionality, highlighting that it’s not just an issue Travelex are facing on their own. In addition to Travelex direct customer base, many other organisations rely on Travelex to service their customer needs. These include some major high-street banks and all their customers. The ramifications of the Travelex ransomware incident has called into question the supply chain resilience of all these affected organisations. If Travelex is only now at the point that they are able to start restoring functionality then the issue is likely to go on for some weeks, if not longer. Many organisations relying on Travelex have suspended services. From cursory research, it doesn’t appear these partners are offering their customers an alternative service. Perhaps they were hoping the issues were going to be resolved quickly. And if you believed their privacy notice, you may be inclined to think such an issue would be resolved pretty quickly. The following is an extract of their Privacy Notice. It’s pretty standard fayre but the security section states that Travelex:
“Will keep your personal data secure and confidential, ensuring that access to your personal data will be limited appropriately only to those who need it to conduct business activities (except as otherwise required by applicable law). We adhere to industry standards for technology and, security and use tested administrative, technical and physical security measures to protect your personal data from unauthorised access, use, modification, disclosure or destruction. We also ensure that our employees undertake annual training in order to uphold these principles and commitments.”
Evidently, some of these standards and security measures were not being applied adequately given the realities of this ransomware incident. If they were, this issue would not still be ongoing, let alone take nearly two weeks to ‘start’ to restore some services.
What can we do to improve our Supply Chain Resilience?
There are a number of things that can be done to improve supply chain resilience. Some are more complex and resource-intensive. Like any issue in business, we recommend that organisations take a risk-based approach (which is not purely based on some rudimentary heatmap and a finger-in-the-air approach to risk management!). The higher the risk, the more robust the mitigation.
Implement an effective Third-Party Risk Management Programme
A robust third-party risk management programme will aid in identifying potential sources of risk in your supply chain resilience. Don’t just conduct a tick-box due-diligence exercise at the start of the arrangement because you want to get the revenue streaming in as soon as possible. Poor due-diligence is only going to cause the revenue to start streaming back out again pretty quickly when things go wrong. Don’t just stop at an initial due-diligence exercise. There must be periodic (dependent on risk) supervision.
Stop Relying on Self-Attestation for High-Risk Vendors
There are a number of these self-attestation programmes around. Cyber Essentials and the CSA STAR Level 1 assessment are examples. The thing is just because someone in an organisation has genuinely answered a questionnaire in good faith doesn’t mean that the organisation is meeting the spirit of that particular certification scheme. Even if they did at a specific time, the schemes are only point-in-time attestations. The day after certification is achieved, everything could simply stop. Lots of organisations have policies but lots of organisations don’t effectively enforce those policies in any meaningful way. The only way to get any form of comfort is to rely on an independent third-party assessment such as ISO 27001 or CSA STAR Level 2/3 or, conduct your own third-party risk assessment. If you can’t conduct your own assessment get someone like Fox Red Risk to come and do the assessment for you. It’s important to caveat that even independent assessments are not completely flawless but they are much more likely to give an objective assessment of the organisation’s security posture and effectiveness.
Contractually Require Security KPIs at Service Management Meetings
Organisations bake Key Performance Indicators and Service Level Agreements into their outsourcing contracts so why not include security Key Performance Indicators (KPIs) too? If a vendor conducts a penetration test, require that critical and high-risk findings are reported alongside the proposed remediation plan (with timings). If an external supervision visit identifies a Major or Minor Non-Compliance, again, require this is reported. It may surprise some organisations to know that this kind of information must be provided when requested if the vendor is processing personal data. Article 28, para 3(h) requires a Processor:
“makes available to the controller all information necessary to demonstrate compliance with the obligations laid down in this Article [28] and allow for and contribute to audits, including inspections, conducted by the controller or another auditor mandated by the controller.”
So, if a Processor is fobbing you off during an audit, then you may want to highlight that they may be in breach of their legal obligations should they not provide information which is reasonable to request. Beware of organisations quoting confidentiality. It’s highly likely you have (or should have) confidentiality clauses in your contracts so confidentiality should not be a barrier to such reasonable requests – and they can also redact identifying information such as IP addresses and hostnames.
Identify Supply Chain Resilience Strategies
We at Fox Red Risk espouse the All-Hazards approach to Operational Resilience. Part of that process is looking at the “PLATS” risk of loss categories. PLATS stands for People, Locations, Assets, Technology and, in the case of this article Supply Chain. Where Supply chain resilience is identified we recommend organisations implement strategies for both short-term and long term supply chain resilience impacts. One of the strategies we recommend is to have a secondary or backup supplier. Having a backup supplier is not simply Googling someone who does the same thing as your current supplier and then whacking that in a Business Continuity Plan. Identifying a backup must start at the procurement phase. Commonly three to four suppliers should be assessed during the procurement phase with the best supplier (not just on cost but weighted against a number of categories) being picked to provide the service. Consideration at this point should be given as to whether to retain the services of the second or third supplier in order that they can be brought onto the pitch very quickly should the primary supplier fail to deliver. Consideration should also be given as to whether a multiple-supplier model should apply (if appropriate). In this arrangement, both suppliers provide the same service (perhaps in different geographical regions). Where one supplier is not available, the other supplier then takes over. Another scenario is to consider in-sourcing as a strategy. This approach can also be applied in both the short-term and long-term.
Test properly AND robustly
The key with all the approaches suggested is that they must be tested effectively. Adopt a testing strategy that has the goal of:
“we will test until something breaks!”
By testing, until something breaks, you will know you have had a truly successful test. If nothing breaks, change the scenario, increase the realism, extend the testing period. Whatever your testing approach, ensure you document your testing plan ahead of time so that it can be robustly challenged.
Supply Chain Resilience – Final thought…
Don’t be afraid to have your assumptions tested, your plan questioned, your strategy ripped apart. It’s better a friend does it than the plan proved to be ineffective. Business Units should develop, implement and test their own resilience strategies to ensure they are fully accountable for the outcomes (good or bad). Supply Chain Resilience must form part of these plans. If you’re not sure whether your plans will pass must, or don’t have a clue…give Fox Red Risk a call!
About The Author
About Fox Red Risk
Fox Red Risk is a boutique data protection and cybersecurity consultancy and Managed Security Service Provider which, amongst other things, helps client organisations with implementing control frameworks for resilience, data protection and information security risk management. Call us on 020 8242 6047 or contact us via the website to discuss your needs.
22301 22301:2019 article 28 awareness bcms BIA business continuity calculating risk change management ciso controller cybersecurity data breach data privacy Data Protection data protection by design data protection officer data protection service Data Subject Access Request DPO DSAR GDPR incident management information security leadership monitoring operational resilience Outsourced DPO Privacy processor risk risk appetite risk management ROI security security as a service small business strategic strategy Subject Access Request tools training transparency vciso virtual ciso

